Security-First Culture (SFC) is an organization-wide commitment where security considerations influence decision-making at every level, from strategic planning to daily operational tasks.
It’s not just about having fancy tech or a dedicated IT team; it’s about making security a core part of how the company thinks and acts. A mindset where every decision, from coding a new app to sending an email, considers “How could this go wrong, and how do we protect against it?”.
Leaders set the tone by prioritizing security, allocating resources, and weaving it into the company’s strategy. Every employee, regardless of their role, understands that they play a critical part in the organization’s security posture.
Main Principles of Security-First Culture
- Proactive Risk Management. Teams don’t wait for incidents to happen. They actively identify, assess, and mitigate risks before they materialize into threats.
- Continuous Learning and Adaptation. Threats evolve, so should your people and your strategies. Regular training, updates, and process improvements are standard practice.
- Transparency and Communication. Open dialogue about security concerns, incidents, and best practices creates an environment where problems are addressed quickly.
- Security by Design. New products, services, and processes are developed with security considerations built-in from the beginning. Security supports innovation; it doesn’t block it.
- Data-Driven Decision Making. Security decisions are based on threat intelligence, risk assessments, and measurable outcomes rather than assumptions or gut feelings.
The principles sound sensible but quite challenging to implement. Transferring to SFC might look like an organizational revolution demanding changes on all levels, from the leadership mindset to everyday practices. And of course it must be quite a recourse-consuming adventure. Is the outcome worth it?
Benefits of Security-First Culture
The advantages of implementing SFC extend far beyond just preventing cyberattacks. But the straightforward outcome of suffering less breaches must certainly be considered. Verizon’s 2022 Data Breach Report says 82% of breaches involve human error, so a security-minded workforce can slash that risk.
Fewer breaches mean less damage: financial, reputational, operational. Preventing even one incident can save millions: the average cost of a data breach exceeded $4 million back in 2023, according to IBM. Besides, if an attack does happen, a prepared organization bounces back faster, minimizing damage and downtime.
Customers, partners, and stakeholders have greater confidence in organizations that demonstrably prioritize security. This translates to stronger business relationships and competitive advantages.
Less obvious but no less valuable benefits include:
- Improved Operational Efficiency: When security practices are integrated into daily workflows, they become second nature, reducing friction and improving overall productivity.
- Regulatory Compliance: A security-first approach makes compliance with various regulations (GDPR, HIPAA, SOX, etc.) more straightforward and less costly.
- Innovation Enablement: Paradoxically, strong security foundations enable organizations to innovate more freely, knowing they have robust safeguards in place.
- Employee Empowerment: When staff feel confident handling threats, they’re more engaged and take ownership of their role in security.

Enrich your threat knowledge with TI Lookup
Learn about TI Lookup and its capabilities to see how it can contribute to your company’s security
Explore more
SFC Champions and Those Who Paid the Price
Several organizations have become benchmarks for security-first culture:
Microsoft: Following significant security challenges in the early 2000s, Microsoft implemented their “Security Development Lifecycle” and “Assume Breach” philosophy, fundamentally transforming their approach to security.
Google: Their “BeyondCorp” zero-trust security model and continuous security innovations demonstrate a deep cultural commitment to security.
Apple: Known for privacy-by-design principles and strong encryption standards across all products and services.
Not every company gets it right (providing us with impressive and didactic examples). These high-profile disasters could’ve been mitigated with a stronger SFC:
Equifax (2017): A failure to patch a known vulnerability led to a breach exposing 147 million people’s data. A lack of proactive monitoring and employee awareness was a key factor.
SolarWinds (2020): A supply chain attack compromised multiple organizations. Inadequate security training and siloed responsibilities left gaps that attackers exploited.
AT&T (Multiple breaches 2023-2024): Repeated incidents affecting millions of customers demonstrate ongoing security culture deficiencies despite previous breaches.
Evaluating Your Current Security Culture
Here’s how to understand where you stand:
| Strong Security-First Culture Indicators | Warning Signs of Weak Security Culture |
| Employees proactively report security concerns | Security seen as “someone else’s job” |
| Security is discussed in regular business meetings | Frequent workarounds to security policies |
| New projects include security requirements from the start | Incident response is chaotic or delayed |
| Incident response is swift and coordinated | Security training completion rates below 90% |
| Regular security training has high participation rates | Security budget cuts during tough financial periods |
| Security metrics are tracked and reported to leadership | Repeated similar security incidents |
Cyber Threat Intelligence as a Pillar of Security-First Culture
Cyber Threat Intelligence (CTI) isn’t just a technical capability — it’s the nervous system of a security-first culture. CTI provides the contextual awareness that transforms reactive security measures into proactive, strategic defense.
Like security-first culture permeates and consolidates every organizational unit and structure, state-of-the-art CTI vendors like ANY.RUN offer solutions to cover security-related challenges on all business levels.
CTI for Enriching Cyber Threat Investigations and Response
Daily security operations rely on CTI to prioritize alerts, contextualize incidents, and guide response efforts. Instead of treating all security events equally, intelligence helps teams focus on genuine threats.
Threat Intelligence Lookup allows employees of any grade to utilize a vast database of fresh Indicators of Compromise (IOCs), Behavior (IOBs), and Attack (IOAs) to instantly collect context for alerts, incidents, and campaigns. The data is continuously updated and derived from the attacks on over 15,000 companies using ANY.RUN’s Interactive Sandbox for hands-on investigations of malware and phishing attacks.
An employee does not have to be a security expert to make a search request like a suspicious IP address and receive an instant verdict that the notorious banking stealer Lumma might have penetrated the perimeter:
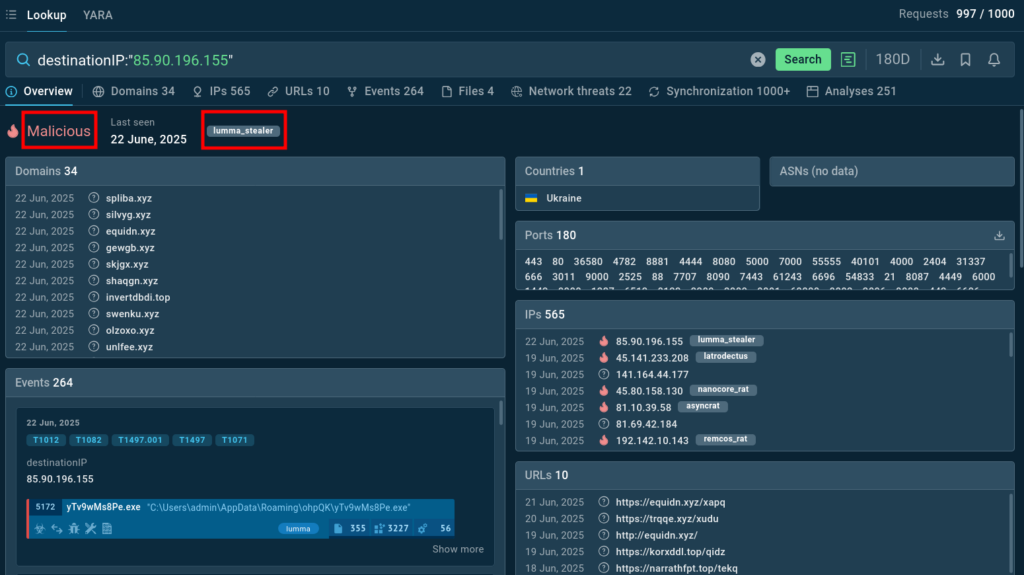
TI Lookup enables teams to quickly gather critical threat context, transforming existing indicators tin actionable insights into the threat to hand to mitigate risks and protect the organization.
CTI for Proactive Threat Monitoring
When it comes to tactical implementation, security tools and controls are configured based on current threat intelligence, ensuring defenses remain relevant as the threat landscape evolves.
Threat Intelligence Feeds provided by ANY.RUN deliver up-to-date curated indicators of compromise like URLs, domains, and IPs, enriched with threat context, to integrate with detection and monitoring systems and identify threats before they become incidents.
CTI For Early Detection of Malicious Files and URLs
Smart threat intelligence solutions improve employees’ ability to make better security decisions in ambiguous situations. ANY.RUN’s Interactive Sandbox makes it possible to analyze any suspicious link, email, or file, and not just get a malicious/benign verdict, but to understand malware’s behavior as well as its operators’ TTPs.
Thanks to interactivity, the sandbox makes it possible to engage with the environment and the threat just like on a standard desktop, detonating every stage of the attack to reveal the final malicious payload.
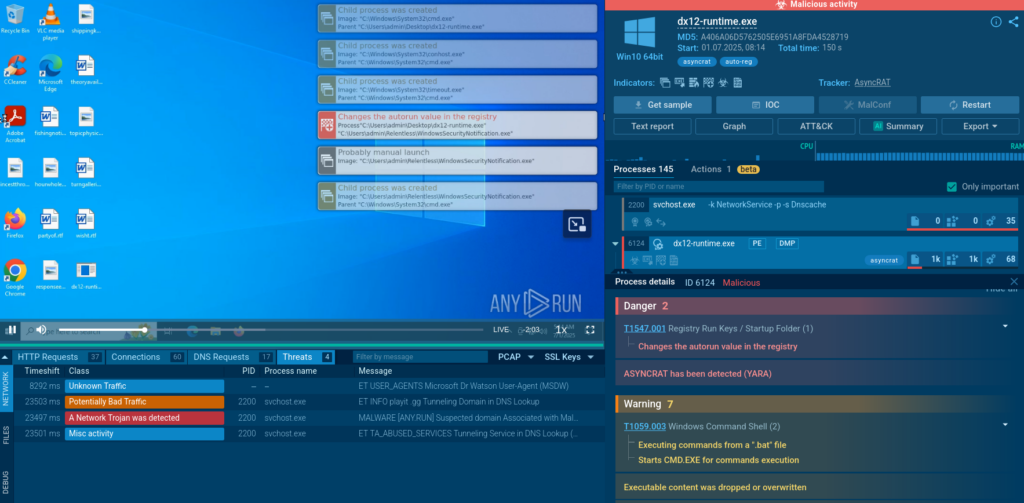
As we can see, the Sandbox file analysis exposes its malicious behavior and labels it as AsyncRAT trojan.
The intuitive interface of the sandbox simplifies malware analysis for junior security professionals and even non-specialists, providing them with a clear understanding of any threat.
Sign up for ANY.RUN’s Interactive Sandbox with a business email
CTI For Improving Security Strategy
In strategic planning, CTI informs long-term security investments by identifying emerging threats and industry-specific risks. When planning business expansion, drafting a security budget for the next quarter, or gathering information on the key cybersecurity risks, it provides crucial context about the current threat landscape.
ANY.RUN’s TI Reports contain manually collected intel on APTs, as well as malware and phishing campaigns that pose a danger to businesses right now. The reports help security teams gain greater visibility into the threats active at the moment and proactively defend their infrastructure.
Step-by-Step Algorithm to Deploy SFC
- Assess Current State: Survey employees, audit processes, and measure metrics like phishing click rates to identify gaps.
- Develop Security Strategy: Align security with business goals, like customer trust or operational continuity. Create comprehensive plan addressing people, process, and technology. Establish policies and security rules (e.g., password standards, MFA use) and integrate them into workflows.
- Train Employees and Implement Tools: (firewalls, encryption, threat intelligence solutions, and monitoring systems to support human efforts).
- Measure and Iterate: Track KPIs (e.g., incident response time, training completion) and refine strategies based on results.
- Review Regularly: Conduct quarterly audits and update tactics to address new threats.
- Celebrate Successes: Recognize and reward security-positive behaviors. Share knowledge and learn from security community.
Final Thoughts
A security-first culture isn’t just about tech — it’s about people, processes, and a shared commitment to staying safe. By embedding cyber threat intelligence into every step, from leadership to daily operations, organizations can stay ahead of attackers, protect their data, and build trust with customers.
Organizations that successfully implement security-first culture supported by robust threat intelligence capabilities don’t just survive in today’s threat environment. They thrive, using their security posture as a foundation for innovation, growth, and competitive advantage.
About ANY.RUN
Over 500,000 cybersecurity professionals and 15,000+ companies in finance, manufacturing, healthcare, and other sectors rely on ANY.RUN. Our services streamline malware and phishing investigations for organizations worldwide.
- Speed up triage and response: Detonate suspicious files using ANY.RUN’s Interactive Sandbox to observe malicious behavior in real time and collect insights for faster and more confident security decisions.
- Improve threat detection: ANY.RUN’s Threat Intelligence Lookup and TI Feeds provide actionable insights into cyber attacks, improving detection and deepening understanding of evolving threats.
Start 14-day trial of ANY.RUN’s solutions in your SOC today
