As we have seen, cyber-attacks can be highly damaging and disruptive. With their insatiable desire to gain power and dominance, attackers can unleash their intent in a stealthy and subtle manner to achieve their goals with precisely targeted and calibrated campaigns on a scale.
These can be multi-stage theatre-level attacks (e.g., Stuxnet/Operation Aurora/Operation Cloud Hopper) or crude attacks like malware distribution or password spraying.
If we look at the security posture which led to these attacks, it has defied expectations and failed to materialize.
The reactive approach could not have any strategic impact and has been reduced to a formality, as it offered no more than some marginal contributions.
We need an alternative approach.
An attack is often wrapped in uncertainty. Its motives are unclear. Its consequences are hard to measure. Its perpetrators are largely anonymous. This uncertainty makes preventing an attack so critical.
When a critical vulnerability is detected, it becomes a window for the attack.
A prevent first approach helps us in making some practical choices: How accessible vulnerability is, how critical it is to operations, and how reliable the system is by having the vulnerability.
These choices shape exposure, which determines how much risk the vulnerability poses in practice. This helps in increasing the awareness of the weakness and becomes a powerful tool for smarter defense by increasing our power over how we respond to it.
The prevent-first approach is about making clear decisions that narrow the attack surface and strengthen defenses with intention, which is not reactive.
You will be able to strategically contain risk with this approach.
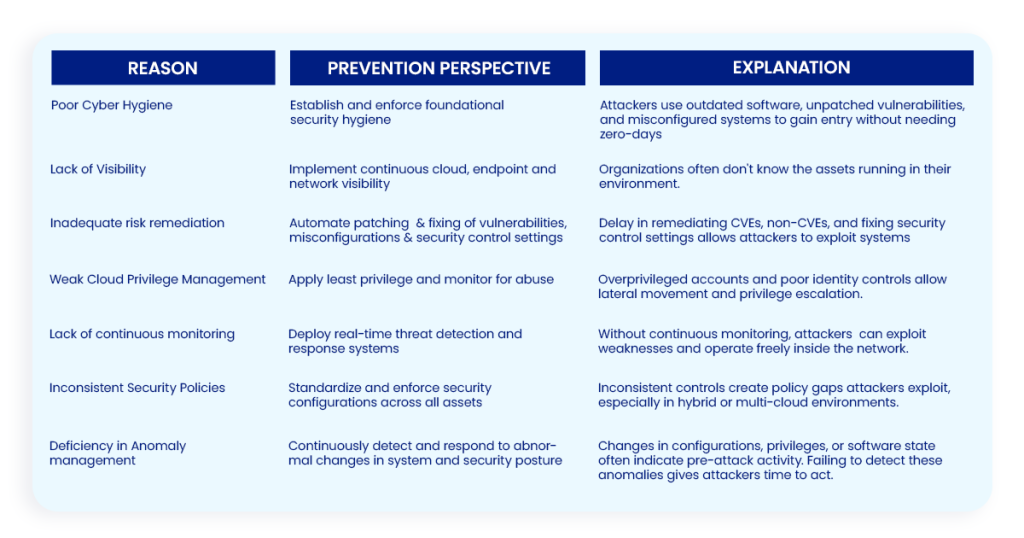
From a prevention perspective, it is not attacker sophistication that wins; rather, it is security gaps that allow them to win.
Here are some fundamental reasons for an attacker’s success and what needs to be done.
Prevention is not about having a first line of defense. It is about how well the business is ready to absorb the risk of a cyber-attack through better resilience. Its responsibility is twofold, protect against attacks and ensure smooth operations despite attack possibilities outside the business environment.
Gaining Long-Term Resilience & a Proactive Risk Posture
Prevent-first isn’t just about early detection. It’s about having a system that can help you act quickly based on early insights into your security gaps. It is an approach designed to show how risk should be perceived, understood, and acted upon.
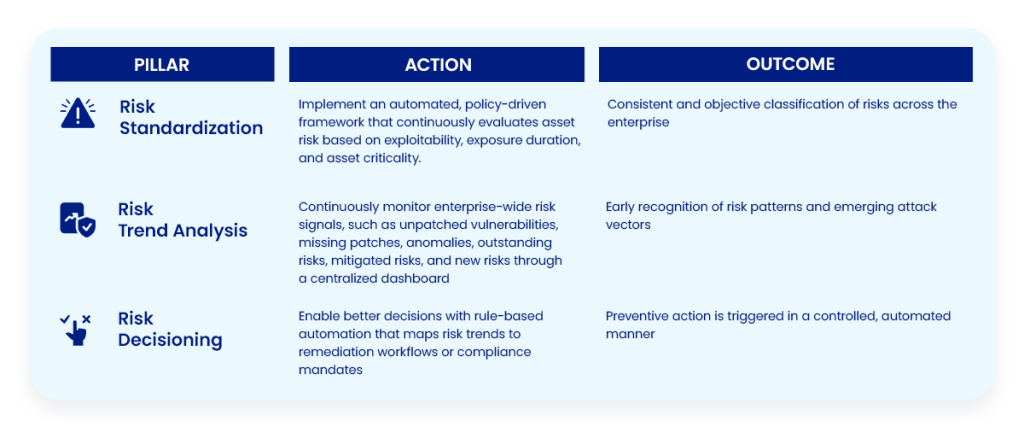
Vulnerability risk can be understood through three key pillars. Risk decisioning, risk trend analysis and risk standardization.
But if you map these pillars to what is happening now in enterprises, we get some disturbing observations.
What is happening?
- Risk Decisioning currently operates in silos with variable thresholds across departments
- Risk Trend Analysis identifies unpatched vulnerabilities, missing patches, etc., but does not show anomalies, outstanding risks, mitigated risks, and new risks lacking unified interpretation
- Risk Standardization is immature, standards and taxonomies differ across teams, tools, and geographies
Security actions are often reactive, triggered by events rather than indicators. There is an over-reliance on detection and response.
Why is this happening?
Here are the root causes.
- The risk data is not consolidated due to siloed tools
- There is no common risk language (scoring method), which makes standardization not possible
- Inability to recognize vulnerability/misconfiguration/anomaly trends due to data silos and sluggish data aggregation
- Lack of coordination between IT & Sec team due to a lack of a unified dashboard, overwhelming alerts, and not knowing what to fix first
Vulnerabilities may be detected but not prioritized correctly because there is no reliable and consistent risk prioritization approach to enable decisions, appetite framework, or decisioning protocol. This allows preventable attacks.
What is likely to happen?
If these gaps persist, it can lead to:
- Increased exposure window between detection and remediation
- Misprioritization of risk leading to attacks on low-visibility vulnerabilities
- Siloed tools can miss early signs of an attack
- Audit failures due to inconsistent standards
What should be done?
We need a platform-driven model to implement the prevent-first approach. It will help us understand and track risk continuously, based on intelligent, automated control before an attack can materialize. This approach is far ahead of the threat-first approach, which is dauntingly opaque, as it can mask risks until they resurface, forcing teams to scramble to fix them. Here is how the prevent-first approach helps in modifying the three pillars we discussed earlier.
To prevent, you need continuous risk prioritization
The prevent-first model helps move from uncertainty to control, continuously and intelligently. For this, there is a need to bring structure, context, and automation into security posture. This is where the three foundational pillars, Risk Standardization, Risk Trend Analysis, and Risk Decisioning, can enable Continuous Risk Prioritization.
Risk Standardization: For Scalable Prioritization
Enterprises are overwhelmed by huge vulnerability backlogs, millions of them. The first step is to plug them in through consistent standardization. When you use the prevent-first model, risk standardization replaces generic scoring models (such as CVSS) with a structured, contextual framework (such as SSVC). Instead of relying on static CVSS scores, SSVC employs AI-driven vulnerability enrichment, giving it deeper meaning:
- Exploitability assessment
- Exposure monitoring
- Asset correlation
- Attack vector analysis
- Vulnerability volume processing
- Business impact analysis
With the power of AI, these models can help standardize risk categorization by recognizing which vulnerabilities pose danger, reducing the noise, and allowing teams to focus on what truly matters.
Know more about SSVC risk prioritization.
Risk Trend Analysis: To Contextualize Vulnerabilities
A CVSS approach treats vulnerabilities as a static record. As you know, vulnerabilities can evolve due to the dynamic nature of threats. This can be based on exploitation trends, exploitation trends, system configurations, and attacker behaviors.
A prevent-first posture implements dynamic risk contextualization using SSVC.
Risk Trend Analysis adds context and clarity to static risk data. Instead of one-time scans or periodic reviews, this pillar emphasizes continuous monitoring of vulnerability risks.
- Clarity on the types of vulnerabilities
- Unpatched vulnerabilities
- Changes in security posture
- Emerging exploit code in the wild & Its POCs
Importantly, it incorporates business context, how critical the vulnerable system is, whether it supports key operations or is exposed to access and reflects true risk.
By using security intelligence, exploit likelihood, and asset criticality using AI, the prevent-first approach can spot vulnerabilities that have the most impact on the organization.
Risk Decisioning: Automating What Matters Most
The last step in continuous risk prioritization is automating the entire decision process. Though many teams are still using siloed, manual approach, which is constrained by delays and inconsistencies.
Automated, AI-driven SSVC approach changes all this. It enables us to:
- Use MITRE attack mapping to automatically categorize risks based on exploitability, automatability, and technical impact
- AI-driven risk categorization to refer to factors such as malware, CISA KEVs, vendor advisories, exploit databases, etc.
- Segregate them into Critical, High, Medium, and Low priority ones
- Enable remediation workflows based on risk thresholds
- Defer low-impact vulnerabilities
- Use ML-driven EPSS (Exploit Prediction Scoring System) to predict the probability/likelihood of exploitation
- Security intelligence integration ensures decisions are continuously evolving with new, updated vulnerability data coming in every day
This is needed as manual risk prioritization using siloed tools cannot scale. The SSVC approach, with its AI capabilities, ensures there is no guesswork about what to fix first.
Know more about EPSS
What are the gains?
By integrating risk standardization, trends and decisioning, the prevent-first approach brings clarity.
- Standardization ensures a common language for risk across business
- Trend Analysis adds context and evolution to risk
- Decisioning acts on this intelligence without delay
It also solves the biggest paradox of security, how to prioritize effectively in the world of infinite vulnerabilities.
Let us pause here and discuss a simple, often used security equation.
Threat =?Vulnerability × Exposure. And since risk is the probability that such a threat will occur, we can say, Risk =?Probability of Threat (vulnerability × exposure)
When viewed through this equation, we need to minimize either vulnerability or exposure so that the outcome (threat) becomes zero and the probability of it becoming a reality becomes less.
Mapping the Security Equation to the Three Pillars
Each Prevent-First pillar contributes to reducing vulnerability and exposure and mitigating threats and risks.

Gaining Strategic Superiority over Attackers
When we look at the equation, Risk =?Probability of Threat (vulnerability × exposure), we can see that when vulnerability or exposure multiples, the risk is high.
With the prevent-first approach, you can achieve strategic superiority by breaking that multiplication at every opportunity. Here is how.
- By Risk Standardization, every vulnerability is contextualized. By assigning precise, business-aligned severity to each vulnerability, you can remediate them before they are exploited
- With Risk Trend Analysis, you’re continually watching shifts in how and where systems can become attackable, E.g., when internal service is suddenly Internet-facing, or POC code for vulnerability in the wild. Early detection lets you remediate or fix the misconfiguration before it is exploited.
- Risk Decisioning ties the above two pillars together: the moment any combination of vulnerability score and exposure state crosses a risk threshold, automated workflows detect and remediate it, ensuring the threat is almost zero.
The Prevent-First equation flips the attacker’s advantage on its head. Rather than reacting after a breach or detection alert, you can act before multiplication of risk occurs, continuously.
This shifts you from a posture where you can continuously reduce the attacker’s strengths. It helps you to gain and sustain strategic superiority over attackers.